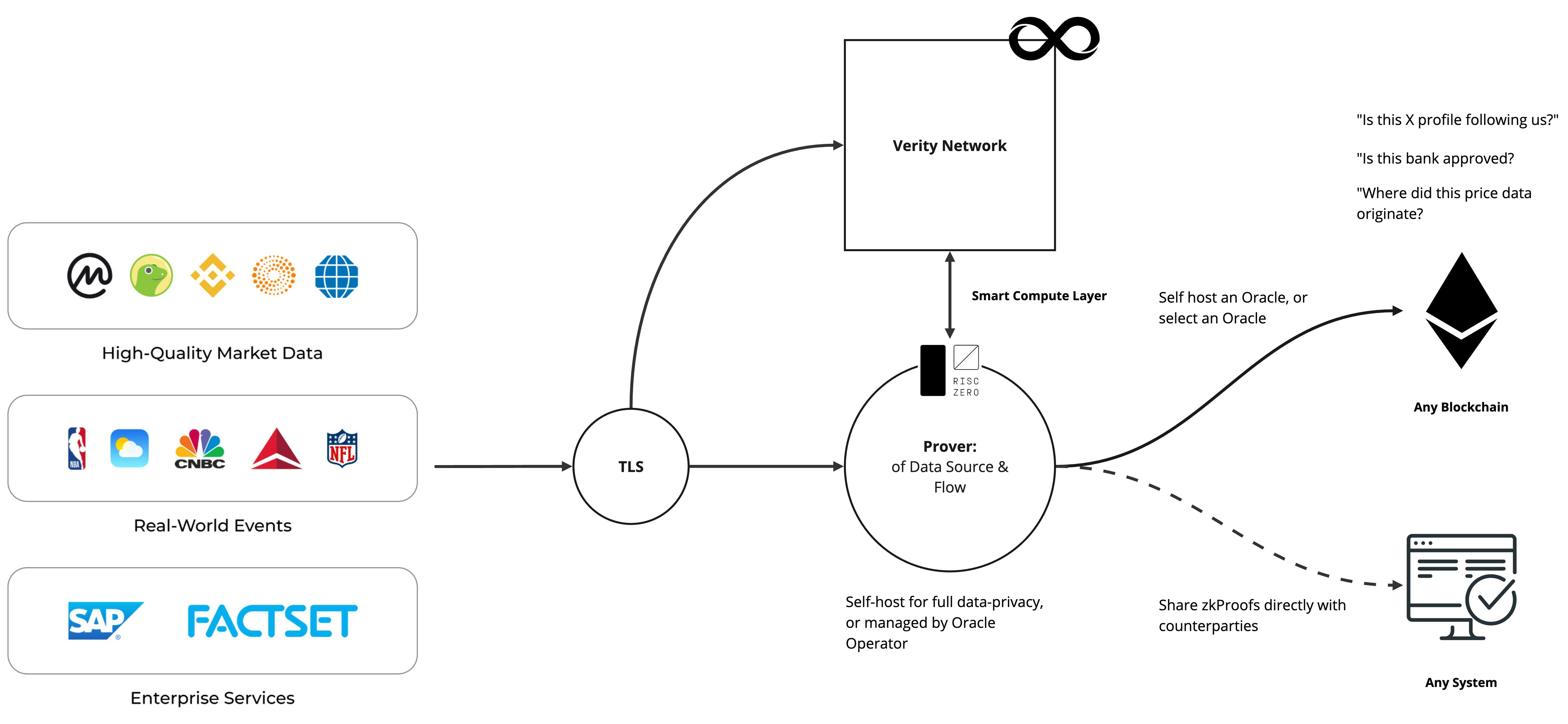
Building a Verifiable Data Pipeline
To create a verifiable data pipeline, we need to:- Familiarise ourselves with generating TLS proofs using the Verity Network CLI.
- Develop a Prover Orchestrator: a server application that programmatically orchestrates TLS proof generation and our verifiable data pipeline starting with the Verity Client. The Verity Client is a library within the Verity Data Processor (VDP) Framework.
- Utilise the VDP Framework, which provides libraries to assist our Orchestrator in processing data derived from our TLS proofs in a completely verifiable manner. Be sure to select the appropriate Verifiable Data Processing Environment (VDPE) for your use case.
- Once we have our Data Flow Proof (DFP), obtained from our VDPE, we can submit our DFP to a blockchain for verification.
Prover Orchestrator Examples
Usher Labs has prepared examples demonstrating how to implement a Prover Orchestrator in various programming languages.- Rust using zkVM for data processing:
- Rust using the Internet Computer for both data processing and as a destination chain:
- (Work In Progress) Typescript using Internet Computer as a precompute for data processing on the destination chain:

