- RiscZero’s zkVM
- The Internet Computer (IC)
RiscZero’s zkVM (ZK VDPE)
RiscZero is the most production-grade zkVM, designed for CPUs with smaller workloads. It is the zkVM of choice for Verity, ensuring stateless Rust development to a limit, providing data processing capabilities, and a portable succinct proof format for verification across various environments, whether on- or off-chain.The Internet Computer (IC VDPE)
The Internet Computer (IC) is a decentralised and replicated compute platform that enables the processing of data in a way that can be verified by a third-party verifier system, typically a destination system within the context of a data pipeline. It achieves this through Chain-key cryptography, a cryptographic primitive specific to the Internet Computer (IC).Verity Data Processor Framework (VDP)
The VDP Framework is designed to support developers building provers of data pipelines with libraries that abstract cryptographic complexities when integrating data with existing prominent blockchains. The VDP streamlines the incorporation of intermediary ZK or IC VDPEs for processing data from its initial state into a new state that blockchains can accept and verify. Once data has been sourced and proofs attesting to the data sources are in place, the data can be transformed and processed with support from the VDP Framework for compatibility with a destination system, such as a prominent blockchain.For example, consider a zkTLS-enabled Oracle that proves various data sources indicating the price of an asset. Within the VDP, these sources can be verified and a weighted aggregation performed, which can then be verified by the destination blockchain.
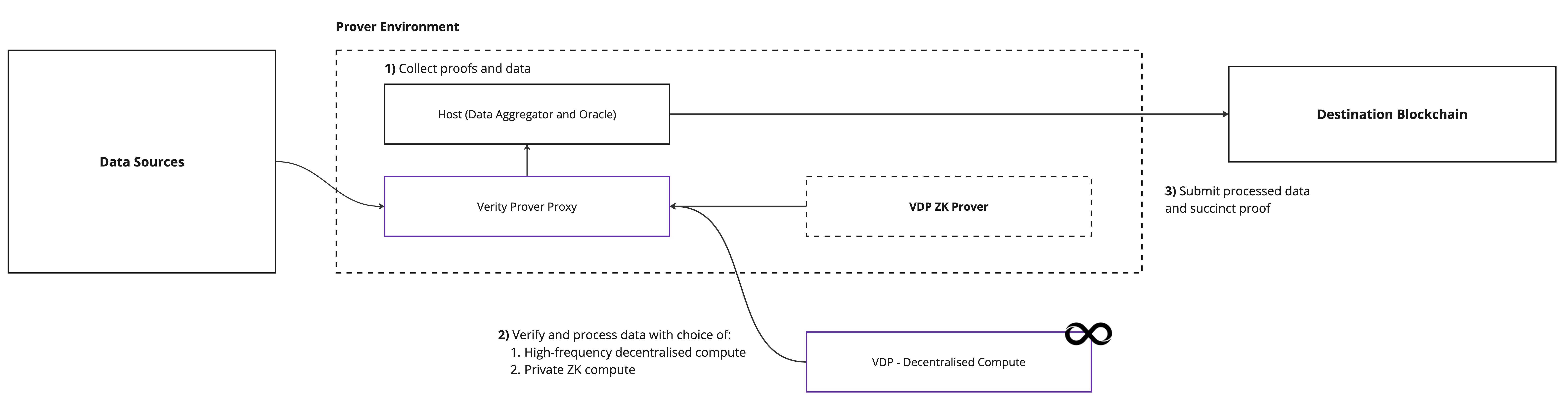
Developer Requirements
Developers adopting the VDP need a programmatic pure (aka stateless) function capable of verifying the sub-proofs and processing the API response data. For now, the Rust programming language is required.VDPE Purpose
The VDP libraries simplify the process of verifying these TLS proofs and their inner sub-proofs.- ZK VDPE: Under the hood, the Verifier is incorporated to share in MPC verification of only public facets of the TLS proof, essentially conducting precompute functions on TLS proofs, minimising ZK proving overhead and time to proof.
- IC VDPE: The Verifier is called via cross-contract invocation, offering a simple, already deployed interface to ensure TLS proofs are verified and valid within the IC.
Framework Flexibility
The framework allows developers to choose between:- ZK (Zero-Knowledge) Computation: Privacy-preserving computation.
- IC (Decentralised) Computation: High-speed public decentralised computation powered by the Internet Computer.
Cryptographic Proofs
Each supported VDPE can produce a succinct cryptographic proof of the data processing outcome.- ZK Computation: Yields a ZK-SNARK based on the Groth16 primitive, directly compatible with blockchains such as Ethereum and other EVM chains.
- IC Computation: Yields an ECDSA signature powered by TSS (Threshold Signature Scheme), where all parties reach consensus over outcomes to form a single signature.

