Primary Implementation
Verity is designed for compatibility with any blockchain. The general-purpose Verifier within the protocol ensures this, however, the choice between VDPEs is left to the Developer to determine how best to adopt and implement data pipelines that serve the best outcomes for their use case.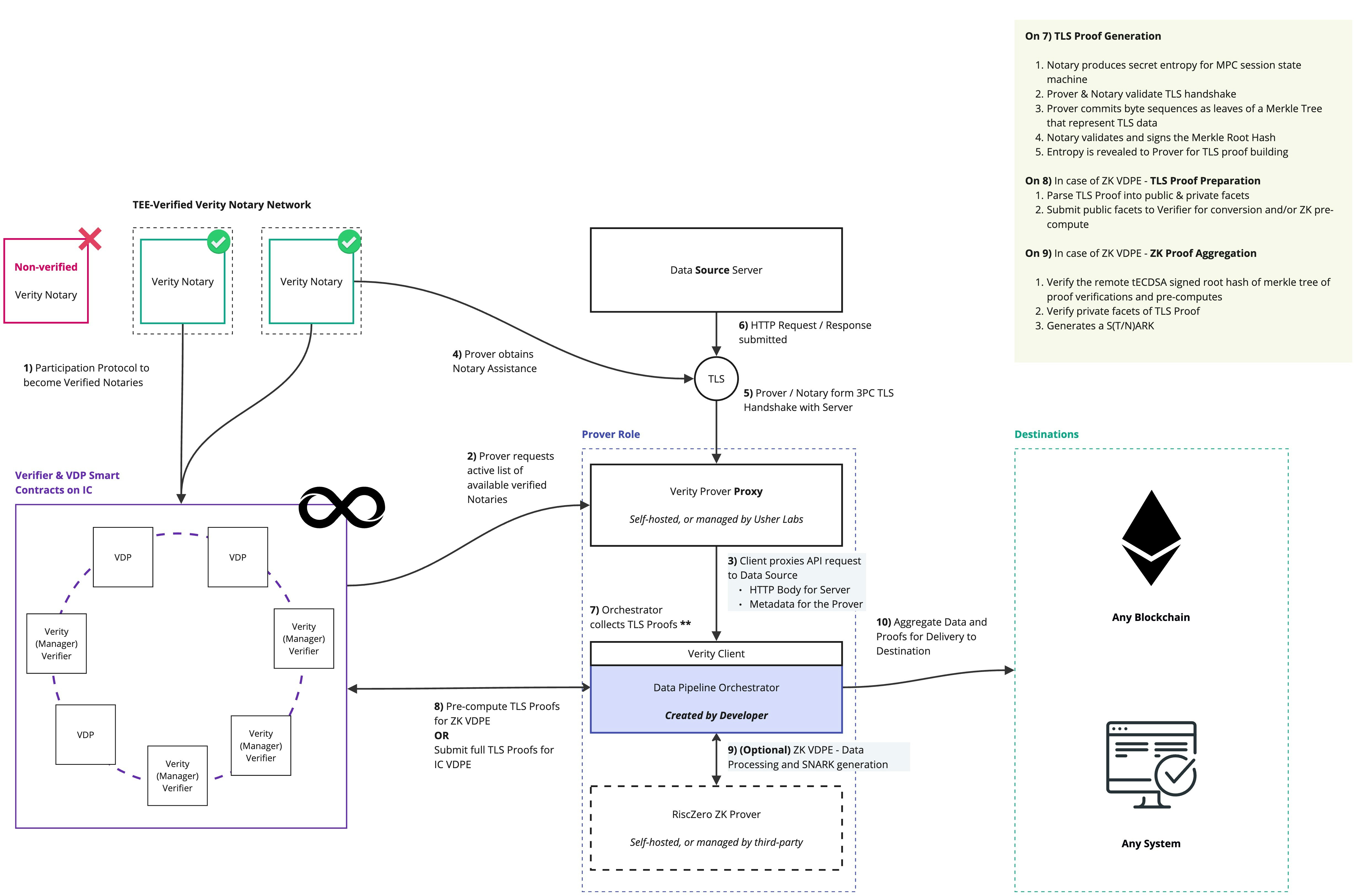
Off Destination
The “Off Destination” implementation is the most common use case for Verity. It involves abstracting as much data processing and orchestration of the verifiable data pipeline off of the destination blockchain as possible. This is ideal for destination blockchains that:- Are expensive to compute on, such as Ethereum.
- Are restricted with respect to their transaction size limits, making them limited with respect to the amount of data they can process.
- Involve Smart Contract programming in languages that are not suited for data processing requirements, such as Solidity.
On Destination
The “On Destination” implementation is a secondary approach for implementing Verity. Here, the Verity Verifier is utilised specifically to ensure cryptographic compatibility with the destination blockchain. However, all subsequent data processing is performed on the destination blockchain. Some Move-based Blockchains such as Rooch Network have proven to be capable of parsing and processing JSON data, for example.Tailored Alternative Implementations
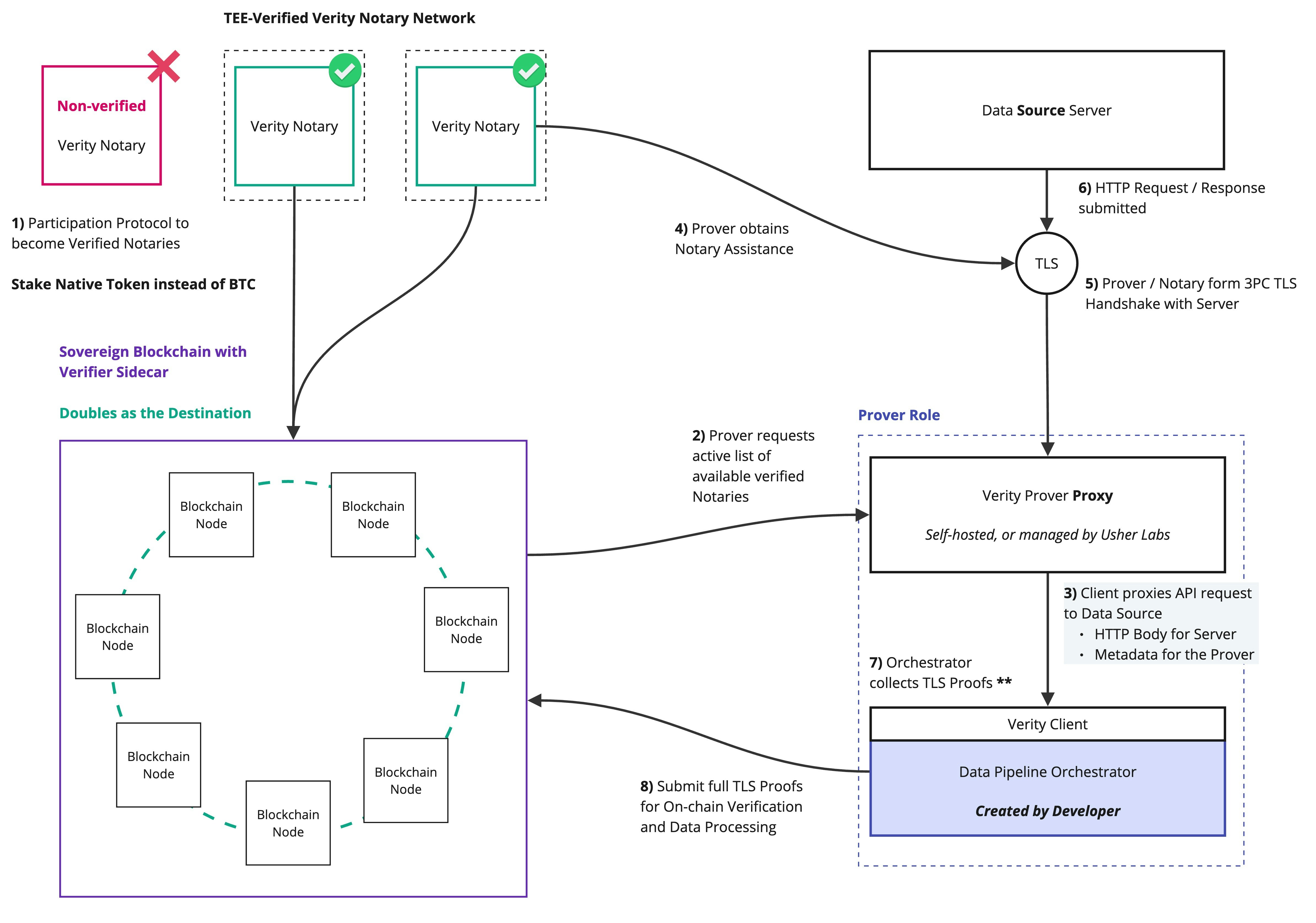
Sovereign Blockchain Extension
Verity’s Verifier serves as the coordination and verification layer of the network. While the Verifier will be deployed for general-purpose use, Verity is designed to empower sovereign blockchains with enhanced capabilities for verifying real-world data. Verifier Sidecars are created to extend blockchain nodes, effectively embedding their role into the base layer of a blockchain.